Contents
Bitcoin blockchain: too much transparency for the black market
For those who haven’t been reading much into the subject, I’d like to say that blockchain is first and foremost a networking technology. It is a kind of immutable distributed ledger that cannot be tampered with. Each cryptocurrency has its own blockchain, that is, a network of participants who interact in a certain way and have certain rights, which depend on the degree of (-de)centralization, the consensus algorithm and other features of the network. By the way, there are already many blockchain projects in finance, logistics, real estate, and insurance, but that is not what we are talking about today. It is important to understand that there are open, closed, and hybrid types of blockchain, and the bitcoin network is one of the first.
It is a decentralized, peer-to-peer network that anyone can join by simply registering a btc wallet anywhere. Transactions are completely transparent and can be viewed on various browsers. The same applies to wallets, which are easy to track.
For example:
- https://www.blockchain.com/explorer (classic btc transaction browser)
- https://blockchair.com/ (searches through 17 blockchains)
Let’s take, for example, one of the wallets in Chatex and look at its history.
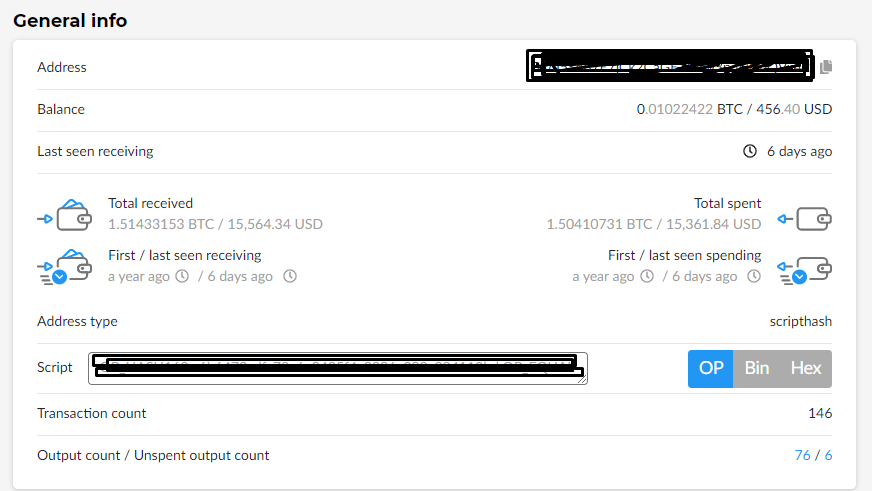
Immediately we see the current balance, transaction history, and the total amount wrapped through this purse. Everyone knows this for a long time, but knowing the transaction history of one wallet, it is easy enough to establish its relationship with another wallet and calculate, for example, the further movement of funds, despite the whole principle of decentralized network, the presence of pools and the use of N addresses for a single transaction.
Example
You buy banned items on the darknet. To buy bitcoins you use crypto-service, where you can’t change your btc-address, and on the darknet market you often forget to click the “Change address” button next to your wallet address. In other words, you have two fixed addresses. Well just theoretically, because even changing the address on the marketplace, you are still in the same pool.
For example, someone knows about it, gets your bitcoin address from the crypto-service and analyzes which address you send money to most often. It is easy to assume that this address is your wallet on the darknet marketplace. This is an extremely crude, technically not entirely correct, but a simple example of the relationship between wallets.
Once you understand the essence of the example, you can understand the following for yourself: bitcoin anonymity is so shaky that it is not even worth talking about it out loud. And there is no need to understand this article as a call to reject bitcoin, because as an investment instrument, it is simply beautiful and has no close analogue, except for DeFi-token YFI, when we talk about the price and its average annual growth rate. But let’s go back to the fact that bitcoin transaction analysis is not that complicated and even using a mixer does not guarantee complete protection, because it can be of poor quality.
For example, a few years ago I wrote an article about ChainAnalysis in my translation of “How the U.S. Government is Studying Blockchain. It is only worth mentioning that thanks to this company hundreds of sellers and ordinary users of the Silk Road darknet site have been de-anonymized and caught.
By the way, ChainAnalysis works all over the world and nothing prevents our law enforcement agencies from turning to them if necessary. The question whether they will do so and spend the budget to investigate cybercrime I will leave unanswered. Just think about how many years our three-headed marketplace has been successfully operating and in what crypto it accepts payment.
“Anonymity” of bitcoin and cryptocurrency in general
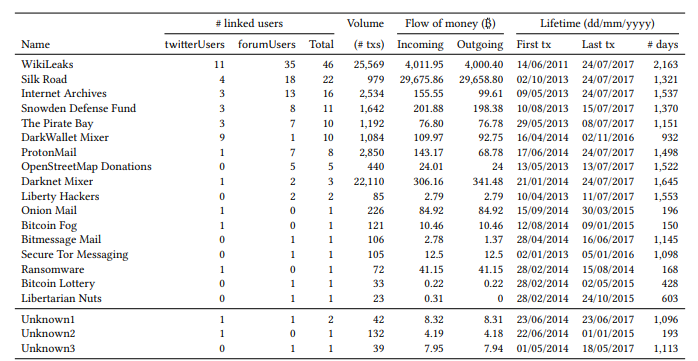
Below you can see an example of what the result of the analysis of bitcoin wallet’s connection with shady services in Tor network looks like. You can read the full study here.
But there is an anonymous crypto, why use bitcoin? I am sure that we should not talk about pseudo-anonymous counterparts like ZCash and Dash as worthy alternatives. For example, there is a study that says that 85% of Zcash transactions are transparent, traceable and public. Of the remaining 15% of private transactions, only 7% are actually private. As for Dash, there’s not much to say after Fernando Gutierrez, marketing director of Dash Core Group, said that “Dash is a cryptocurrency for payments, not for anonymity. Draw your own conclusions. Perhaps the only noteworthy anonymous cryptocurrency to date remains Monero. The only more or less memorable fakap of this crypto is the possibility of XMR theft due to wallet vulnerabilities, which was quickly enough patched.
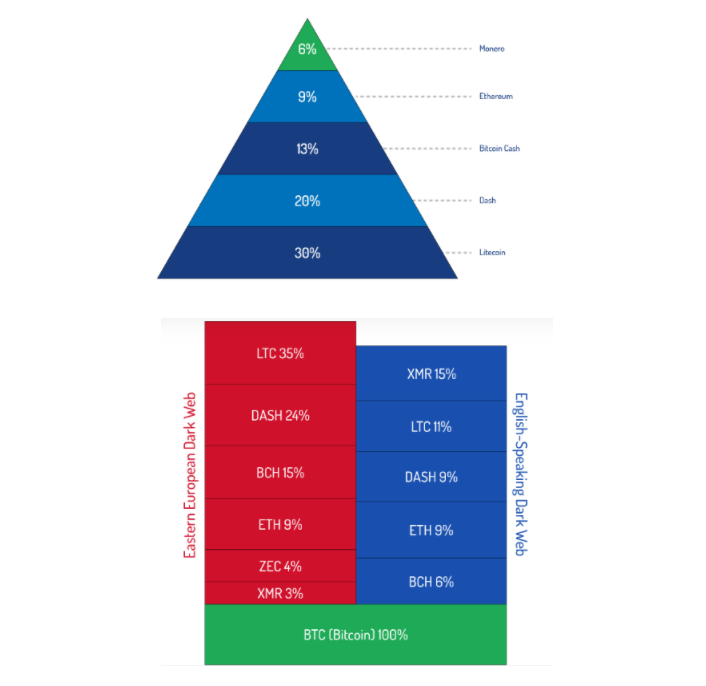
In conclusion of this section, I would like to spit in the face of the skeptics who snorted and laughed dismissively about the applicability of LTC in the shadow segment of the Internet. MingleJingle, a new version of MimbleWimble, will start working in the Litecoin testnet this year. And that means the following:
Litecoin developer David Burkett, who is responsible for the MimbleWimble integration, gave an update on its implementation. He said that significant progress has been made and the initial code will be ready and available for review on March 15.
The MimbleWimble implementation project in Litecoin has been in development for over a year, and the MimbleWimble Extension Blocks (MWEB) test network was launched last September. Burkett recently turned the community's attention to MingleJingle, a new offering from leading developer RandomX Tevador.MingleJingle is a redesign of the original MimbleWimble protocol, offering completely non-interactive transactions. This means that the sender only needs to know the recipient’s address generated from the two public keys. Other important features include addresses that cannot be linked to wallets, and transaction outputs for which no addresses can be determined.
According to Burkett, Tevador’s extensive experience with hidden Monero addresses has led to a number of innovations in the project, as well as improvements in MWEB addressing and output structure. Burkett added additional tweaks to the overall mechanism for hiding transaction details, and said the code is now ready for the new test network. It will contain all the consensus, P2P and wallet code needed to support MWEB.
By the way, the original articles about darknet that I refer to in the section above were on DeepDotWeb, which now looks like this. The fight of Europol and the FBI against the darknet was so extensive that they even shut down news sites a few years ago and I still cannot find decent analogues that would cover operations against the shadow segment of the Internet of services like Interpol, FBI, NSA, CIA and others. In other words, they don’t want us to know the extent.

Methods to de-anonymize bitcoin users
Active Methods.
- Social Engineering. Do I need to explain anything here? The standard toolkit of a social engineer: OSINT + misleading techniques for communicating with the victim. Faking, phishing, sending a stiler, whatever. Not a particularly effective method in the wrong hands.
- P2P network analysis. It is known that the bitcoin network has two classes of nodes: servers and clients. The difference between them is that clients are nodes that do not accept incoming TCP connections, while servers do. Clients and servers have different protocols and anonymity issues. For example, clients do not relay transactions. This is why the focus of de-anonymization techniques is on servers. Absolutely all P2P network attacks are based on the mechanism of transactions in the system. In theory, a hacker can capture the IP address that initiated a broadcast transaction and start “sniffing” the traffic (classic MitM). Various researchers have previously used so-called “routing protocols” (note Flooding) to link a user’s IP address to their Bitcoin network identifier. In 2015, the Bitcoin community responded to such attacks and changed the protocol to a different one, called “diffusion” in the cipherpunk environment. The attacks described above use a supernode (a large node) that connects to active bitcoin nodes and eavesdrops on all transactional traffic relayed by those nodes. With this technique, the accuracy of de-anonymization is around 30%, but there is a more advanced version of the attack that tests for higher accuracy.
Passive methods
One group of passive methods is based on OSINT technology. In other words, it is an open-source search. There are a lot of different “hacker” search engines for discovering specific data. Examples of such services are:
https://www.shodan.io
https://spyse.com/
https://www.zoomeye.org/And yes, these are just search engines, there are other tools, much more serious and effective, but I suggest not focusing on them and go already to the methods of deanonymization.
Direct correlation.The simplest, like the Infusoria shoe, method of deanonymization. The search for mentions of the address in public sources (e.g., on bitcoin forums) and further correlation of the address to the digital identity of the user. For example, user’s nickname will coincide on three different bitcoin forums, but only one of them will contain BTC address in account’s signature. It works badly, but there is still a chance of success.
- multiple entry heuristics
The proposed method can be called multiple-entry transaction heuristics. For the bitcoin network in 2021 there are no other transactions: you always see N senders and much less N recipients in a single transaction. The authors of the study claim that it is possible to determine which addresses belong to a bitcoin recipient by applying a special heuristic algorithm, but it won’t work without a certain set of inputs.
- address change heuristics
We all know that bitcoin network is constantly generating new addresses, somewhere it happens automatically (after every transaction in blockchain.info), somewhere it needs to be done manually (like on triple-header). In essence, your first real bitcoin address does not disappear from the network and stays with you, that is why if a person sends money to your address that is no longer valid, it will still come. Have you ever noticed that? Knowing this peculiarity of the network, you can get to the original user’s wallet through the same heuristic algorithm and search for matches in the transaction history.
A word of caution here: all these heuristics work only with a certain set of data. It takes careful OSINT reconnaissance and preparation of an impressive dataset.
- Clustering Method.
The authors of this study proposed a bitcoin network clustering method based on the two aforementioned heuristics. Using the first heuristic, the researchers were able to partition the network into 5,579,176 user clusters. The authors used a transaction graph and an address graph (see below) The researchers extended the second heuristic, because if an attacker can identify changed bitcoin addresses, he could potentially cluster not only input addresses (according to heuristic 1), but also changes to those addresses.
Overall, the authors proposed a new clustering heuristic based on address changes, allowing clustering of addresses belonging to the same user. Using the proposed method allowed the researchers to identify the addresses of crypto exchanges and some bitcoin casinos using only a small number of identified network transactions.
- Fingerprinting
In this paper, the authors show that any third-party web tracker can de-anonymize cryptocurrency users who use crypto to pay on some online store website using your cooke files. There are 2 variants of the attack in this method:
Single Transaction Network. The purpose of the attack is to link the user of an online store or other web service to a specific transaction in the blockchain. If the tracker has a bitcoin address feature, it's a done deal. Another option is when the tracker remembers the amount of the transaction and the time. This data is used to find the address in the network's transaction history for the purpose of further de-anonymization.
Cluster crossing. The goal of the attack is to link two purchases of the same user to the bitcoin blockchain. Here, the attacker identifies a cluster of addresses that include the victim's addresses and looks for intersections between the addresses through the graph method.- The graph method
As it is already clear, the confidentiality of a bitcoin wallet owner is quite fragile. Public bitcoin address is anonymous only when no one knows the owner and can not even assume what kind of transactions are performed through a purse. That’s why many people recommend using disposable bitcoin wallets for black market transactions. One wallet = one transaction.
In this study, the authors used the so-called Page Rank method in the form of a classical graph. The main feature of the method is to identify large bitcoin wallets, which are related to shadow marketplaces and gambling sites, because they are the main bitcoin concentrators in the darknet.
Mixers, KYC and AML
First about mixers. Initially, a mixer is needed to confuse transactions and whitewash your bitcoin that was obtained by criminal means. For example, you sold drugs on the darknet and want to legalize the proceeds. The mixer has its own pool of bitcoin addresses, you run your money through N addresses and get “white” bitcoin at the output. The amount of commission depends on the number of addresses used, and this can be adjusted. But not every mixer can please you with its honesty.
As practice shows, one of the popular mixers is a darknet project and the bitcoins you get are over dirty. There is little point in such a mixer and it is more harmful than useful. Finding a reliable mixer that sends your money accurately, uses a reliable pool, and whitens bitcoins by tricking AML (see below) is no easy task. You’ll either get scammed, the mixer will be empty, or you’ll get lucky and find a reliable service. Each of the mixers should be sought through DuckDuckGo, check it with @cryptoaml_bot and see the results. Below I attach a screenshot of bitcoins transferring through low-quality mixer that is close to darknet marketplace. By the way, the availability of a mirror at the mixer does not always indicate its reliability and is more of a plus than a minus, but the fact is clear: the service is useless.
@cryptoaml_bot evaluates the risk level of your transaction and it has a “Mixer” category, which makes it clear that it can detect bitcoins from a bad mixer, which are also in the high risk category.
It would seem, well it evaluates and evaluates, what difference does it make? But there is a difference, because the same Chatex recently connected to AML and now also evaluates incoming transactions. In other words, now it became much more difficult to sell dirty bitcoins for fiat through this service. Although it is an excellent P2P crypto exchange in Telegram, which had no other choice: either remain a simple exchanger or grow into a full-fledged crypto exchange.
KYC and AML
KYC – Know Your Customer or Know Your Client. This is the principle of financial institutions (banks, exchanges, crypto-exchanges, etc.), obliging them to identify the counterparty before conducting a financial transaction. In other words, it is the verification of you in the service by providing you with documents proving your identity.
AML – Anti-Money Laundering. To be quite precise, the acronym should have been longer, AML CFT CWMDF – anti-money laundering and counter-terrorist financing and counter-weapons of mass destruction financing.
That is the full mission of the non-state international organization Financial Action Task Force on Money Laundering.
KYC is more of a part of AML. The vast majority of crypto exchanges, from Binance to Kucoin, have long had AMLs in place, identifying users and monitoring their transactions. And that’s fine from a white business point of view, but it’s a stick in the mud for shady movement lovers. Often Binance simply does not accept a transaction from the “Dark Market” or “Mixer” category, and then you are left to look for a buyer in Telegram chats and hope that he will buy your bitcoin.
